Get tailored blockchain and copyright Web3 material sent to your app. Earn copyright benefits by learning and finishing quizzes on how selected cryptocurrencies do the job. Unlock the way forward for finance Along with the copyright Web3 Wallet, your all-in-just one copyright wallet in the copyright application.
Policymakers in The us should really in the same way make use of sandboxes to test to search out more practical AML and KYC answers with the copyright space to make certain powerful and effective regulation.,??cybersecurity steps may perhaps turn out to be an afterthought, especially when organizations absence the cash or staff for these steps. The condition isn?�t unique to These new to enterprise; even so, even properly-proven providers may perhaps Enable cybersecurity tumble to your wayside or may possibly absence the training to comprehend the quickly evolving threat landscape.
Policy remedies ought to place much more emphasis on educating marketplace actors close to major threats in copyright along with the role of cybersecurity even though also incentivizing greater protection standards.
Plainly, This really is an unbelievably beneficial enterprise for that DPRK. In 2024, a senior Biden administration Formal voiced fears that all over 50% with the DPRK?�s overseas-currency earnings arrived from cybercrime, which incorporates its copyright theft actions, and also a UN report also shared promises from member states which the DPRK?�s weapons plan is essentially funded by its cyber functions.
This incident is greater than the copyright market, and this kind of theft is usually a make a difference of worldwide stability.
These menace actors were being then capable to steal AWS session tokens, the non permanent keys that let you ask for temporary credentials on your employer?�s AWS account. By hijacking active tokens, the attackers have been ready to bypass MFA controls and achieve access to Safe and sound Wallet ?�s AWS account. By timing their efforts to coincide click here Using the developer?�s usual work hrs, Additionally they remained undetected until the actual heist.
 Richard "Little Hercules" Sandrak Then & Now!
Richard "Little Hercules" Sandrak Then & Now!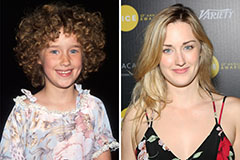 Ashley Johnson Then & Now!
Ashley Johnson Then & Now! Elin Nordegren Then & Now!
Elin Nordegren Then & Now! Soleil Moon Frye Then & Now!
Soleil Moon Frye Then & Now! McKayla Maroney Then & Now!
McKayla Maroney Then & Now!